Risk Audit
Risk OverviewConfidentialityData Confidentiality ClassificationIntegrityAvailabilityOverall Residual RiskGenerating Risk ReportsReporting Service Data CompletionIT Risk Audit - Overview
Risks are divided into 3 categories:
 | Confidentiality | : - The risk of unauthorised access to data |
 | Integrity | : - The risk of data being changed or incorrect |
 | Availability | : - The risk of the service or data not being available when needed |
This 

 classification is a common way of representing risks in security standards such as ISO-27001
classification is a common way of representing risks in security standards such as ISO-27001
IT Risk Audit - Confidentiality
The confidentiality risk is gauged by the type of data stored in, or captured by the service.
For instance course & subject information may be a 1, whereas student identity information might be a 7.
Each data type is given a confidentiality level in a central table (Data Confidentiality Classification).
For each service we want to set a Target  which is determined by the confidentiality of the data stored, and an Actual
which is determined by the confidentiality of the data stored, and an Actual  which is determined by what controls are in place to protect the data.
which is determined by what controls are in place to protect the data.
Actual  is determined by the answers to the following questions. The scores for each control are added up totalling in the Actual
is determined by the answers to the following questions. The scores for each control are added up totalling in the Actual  .
.
| Question | Answer | Score |
| Equipment Access | Remote Desktop | 0.0 |
| Equipment Access | Other | 0.0 |
| Equipment Access | Telnet | 0.0 |
| Equipment Access | SSH | 1.0 |
| Equipment Access | Other Encrypted | 1.0 |
| Equipment Access | Console Only | 2.0 |
| Equipment Access | Not Applicable | 2.0 |
| Equipment Access IP Restrictions | No Restrictions | 0.0 |
| Equipment Access IP Restrictions | Restricted to organisation IP addresses | 1.5 |
| Equipment Access IP Restrictions | Restricted to engineers IP addresses | 1.75 |
| Equipment Access IP Restrictions | Not Applicable | 2.0 |
| Equipment Access IP Restrictions | No Network Connection | 2.0 |
| Equipment Location | Office/Location (UnSecured) | 0.0 |
| Equipment Location | Office/Location (Secured) | 0.5 |
| Equipment Location | Communications Room | 0.75 |
| Equipment Location | Not Applicable | 1.0 |
| Equipment Location | Secure Data Centre (Single) | 1.0 |
| Equipment Location | Secure Data Centres (Multiple) | 1.0 |
| Firewall | No | 0.0 |
| Firewall | Not Applicable | 1.0 |
| Firewall | Restricted by firewall or ACL | 2.0 |
| Lifecycle | Emerging | 0.0 |
| Lifecycle | Retire | 0.0 |
| Lifecycle | Contain | 0.5 |
| Lifecycle | Core | 1.0 |
| Service Type | Other | 0.0 |
| Service Type | Bespoke | 0.0 |
| Service Type | Cloud | 1.0 |
| Service Type | Open Source | 1.0 |
| Service Type | Commercial Off The Shelf (COTS) | 1.0 |
| User Interface Connection | Connects Over Network (e.g. HTTP) | 0.0 |
| User Interface Connection | Runs On Local PC | 1.0 |
| User Interface Connection | Connects Over Secure Network (e.g. HTTPS) | 1.0 |
| User Interface Connection | Client/Server type connection | 1.0 |
| User Interface Connection | Not Applicable | 1.0 |
| User Interface IP Restrictions | No Restrictions | 0.0 |
| User Interface IP Restrictions | Restricted to Organisation IP addresses | 1.5 |
| User Interface IP Restrictions | Not Applicable | 1.75 |
| User Interface IP Restrictions | No Network Access | 1.75 |
| User Interface IP Restrictions | Restricted by Port | 2.0 |
| User Interface IP Restrictions | Restricted to a subset of Organisation IP addresses | 2.0 |
| User Interface Login | No Usernames or Passwords | 0.0 |
| User Interface Login | Cloud Usernames & Passwords (Google/Other) | 0.5 |
| User Interface Login | Windows Login | 1.0 |
| User Interface Login | Not Applicable | 1.75 |
| User Interface Login | Local Usernames & Passwords | 1.75 |
| User Interface Login | Central Organisation Usernames & Passwords | 2.0 |
 Note the priority of a service (Service Restoration Priorities) is not taken into consideration when looking at confidentiality as any service is equally vulnerable to hacking regardless of how important it is to the organisation.
Note the priority of a service (Service Restoration Priorities) is not taken into consideration when looking at confidentiality as any service is equally vulnerable to hacking regardless of how important it is to the organisation.
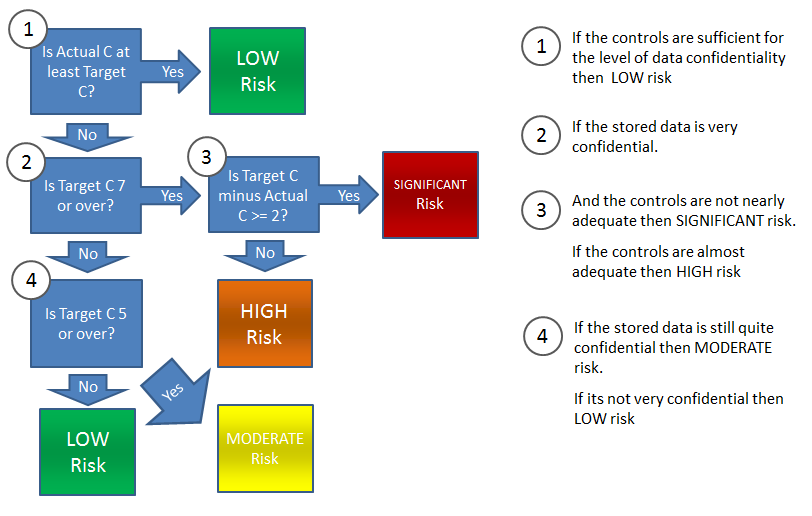
IT Risk Audit - Data Confidentiality Classification
By default data is catalogued with the following confidentiality:
| Data Type | Confidentiality Score |
| Alumni & Advancement > Advancement Identity & Demographics > Alumni | 7 |
| Alumni & Advancement > Advancement Identity & Demographics > Donor | 7 |
| Alumni & Advancement > Alumni Enquiries | 5 |
| Alumni & Advancement > Fundraising Campaigns | 5 |
| Alumni & Advancement > Giving (to us) | 7 |
| Enterprise Content > Commercial IP | 7 |
| Enterprise Content > Email | 5 |
| Enterprise Content > Graphics & Media | 5 |
| Enterprise Content > Intranet Web Sites | 5 |
| Enterprise Content > Performance Measures | 5 |
| Enterprise Content > Project Register | 5 |
| Enterprise Content > Public Web Sites | 1 |
| Enterprise Content > Strategic Funding | 0 |
| Enterprise Content > Strategic Initiatives | 5 |
| Enterprise Content > Strategic Plans | 5 |
| Finance > Budgets & Forecasts | 7 |
| Finance > Chart of Accounts | 3 |
| Finance > Financial Delegations | 3 |
| Finance > Insurance > Insurance Policies | 3 |
| Finance > Insurance > Liabilities & Claims | 5 |
| Finance > Procurement > Invoices | 5 |
| Finance > Procurement > Purchase Orders | 5 |
| Finance > Procurement > Receipt/Delivery | 4 |
| Finance > Procurement > Requisitions | 5 |
| Finance > Procurement > Vendors | 3 |
| Finance > Transactions | 5 |
| Marketing > Event Management | 3 |
| Marketing > Marketing Campaigns | 5 |
| Marketing > Marketing Resources | 3 |
| Other > Administration > Committees/Teams | 3 |
| Other > Administration > Meetings | 5 |
| Other > Administration > University Senate | 1 |
| Other > Enterprise Governance and Compliance > Accreditation | 1 |
| Other > Enterprise Governance and Compliance > Audit Plans | 7 |
| Other > Enterprise Governance and Compliance > Audit Reports & Work Papers | 7 |
| Other > Enterprise Governance and Compliance > Board/Committee Records | 7 |
| Other > Enterprise Governance and Compliance > Contracts | 7 |
| Other > Enterprise Governance and Compliance > Feedback | 5 |
| Other > Enterprise Governance and Compliance > Hazards | 7 |
| Other > Enterprise Governance and Compliance > Improvement Action | 5 |
| Other > Enterprise Governance and Compliance > Misconduct Investigations | 7 |
| Other > Enterprise Governance and Compliance > OH&S Incidents | 7 |
| Other > Enterprise Governance and Compliance > Partnership Agreement/MOUs | 7 |
| Other > Enterprise Governance and Compliance > Policies | 5 |
| Other > Enterprise Governance and Compliance > Procedures | 5 |
| Other > Enterprise Governance and Compliance > Regulatory Compliance Certifications | 7 |
| Other > Enterprise Governance and Compliance > Risks | 7 |
| Other > Enterprise Governance and Compliance > Services | 3 |
| Other > IT Services > Service Desk Requests | 5 |
| Other > IT Services > Work Orders/Change Requests | 3 |
| Other > Medical Records | 7 |
| Other > Organisation > Organisation Structures | 1 |
| Other > Organisation > Organisation Unit Types | 1 |
| Other > Organisation > Organisation Units | 1 |
| Other > System Operational Data | 0 |
| Other > System Operational Data > Directory Services Data | 5 |
| Other > System Operational Data > Firewall Configuration Data | 5 |
| Other > System Operational Data > Hostmaster Configuration Data | 3 |
| Other > System Operational Data > IP and Subnet | 0 |
| Other > System Operational Data > Networking Data | 0 |
| Other > System Operational Data > Postmaster Configuration Data | 3 |
| Other > System Operational Data > VPN Configuration Data | 5 |
| Other > System Operational Data > Webmaster Configuration Data | 3 |
| Property Management > Construction Project Administration | 5 |
| Property Management > Facilities | 1 |
| Property Management > Leases | 5 |
| Property Management > Locations/Sites | 1 |
| Property Management > Maintenance & Work Orders | 3 |
| Property Management > Notice of Works | 1 |
| Property Management > Occupancy | 3 |
| Property Management > Other Assets | 5 |
| Property Management > Parking Fines | 5 |
| Property Management > Parking Permits | 5 |
| Property Management > Room Bookings | 3 |
| Property Management > Rooms | 1 |
| Property Management > Security > Access > Security Access Keys | 5 |
| Property Management > Security > Access > Security Access PIN | 5 |
| Property Management > Security > Access > Security Access Swipe Card | 5 |
| Property Management > Security > Alarms | 5 |
| Property Management > Security > Incidents | 7 |
| Property Management > Vehicle Fleet | 5 |
| Research > Animal Information | 7 |
| Research > Library Resources | 5 |
| Research > Research Administration > Creative Work Management | 1 |
| Research > Research Administration > Ethical Approvals | 5 |
| Research > Research Administration > Patent Management | 1 |
| Research > Research Administration > Plant Breeders Rights | 1 |
| Research > Research Administration > Publication Management | 1 |
| Research > Research Administration > Registered Design Management | 1 |
| Research > Research Grants & Projects | 7 |
| Research > Research Outputs > Creative Works | 3 |
| Research > Research Outputs > Patents | 7 |
| Research > Research Outputs > Publications | 3 |
| Research > Research Outputs > Registered Designs | 7 |
| Research > Research Outputs > Research Data | 7 |
| Research > Research Resources | 5 |
| Staff > Annual Review | 5 |
| Staff > Careers | 1 |
| Staff > Contact Details > Phone Numbers (fixed lines and mobiles) | 0 |
| Staff > Contact Details > Physical location | 0 |
| Staff > Contact Details > Telephone usage records | 0 |
| Staff > Contact Details > Type of equipment (end user phone device) | 0 |
| Staff > Contact Details > Voicemail accounts | 0 |
| Staff > Enterprise Agreement > Hours & Leave Entitlements | 1 |
| Staff > Enterprise Agreement > Payscales & Allowances | 1 |
| Staff > Position Management | 3 |
| Staff > Recruitment > Applications & Job Offers | 7 |
| Staff > Recruitment > Vacancies & Advertisements | 1 |
| Staff > Salary & Payroll | 7 |
| Staff > Staff Expertise | 3 |
| Staff > Staff Identity & Demographics | 7 |
| Staff > Staff Leave | 5 |
| Staff > Staff Placements > Classification | 7 |
| Staff > Staff Placements > Hours & Work Patterns | 5 |
| Staff > Staff Placements > Loading | 7 |
| Staff > Staff Placements > Organisation Unit | 3 |
| Staff > Staff Placements > Split appointments | 0 |
| Staff > Staff Qualifications | 3 |
| Staff > Timesheets | 5 |
| Staff > Training History | 5 |
| Staff > Work Allocation > Academic Workload Models | 5 |
| Staff > Work Allocation > Staff Rosters | 5 |
| Student > Configuration Items | 3 |
| Student > Student & Academic Careers > Graduation Eligibility | 5 |
| Student > Student & Academic Careers > RHD Candidatures | 3 |
| Student > Student & Academic Careers > Student Grievances | 7 |
| Student > Student & Academic Careers > Student Program Enrolments > Class Sign-Ons | 7 |
| Student > Student & Academic Careers > Student Program Enrolments > Course Enrolments | 5 |
| Student > Student & Academic Careers > Student Program Enrolments > Evaluations | 7 |
| Student > Student & Academic Careers > Student Program Enrolments > Results | 5 |
| Student > Student Applications > Program Applications | 5 |
| Student > Student Applications > Scholarship Applications > Academic Scholarships | 5 |
| Student > Student Applications > Scholarship Applications > Equity/Diversity Scholarships | 7 |
| Student > Student Applications > Student Offers & Admissions | 5 |
| Student > Student Applications > Student Prior Learning | 5 |
| Student > Student Enquiries | 5 |
| Student > Student Identity & Demographics > Admitted Students | 7 |
| Student > Student Identity & Demographics > Prospective Students | 7 |
| Student > Student Misconduct | 7 |
| Teaching & Learning > Academic Programs | 1 |
| Teaching & Learning > Course Material & Resources | 5 |
| Teaching & Learning > Course Plans | 1 |
| Teaching & Learning > Courses | 1 |
| Teaching & Learning > Teaching Periods | 1 |
IT Risk Audit - Integrity
The integrity requirements for the service depends on the system that is using it. Getting a students name wrong in the student portal may be embarrassing, but it's far more important it is correct when printing their diploma.
For each service we want to set a Target  which is determined by answers to the folloiwng questions:
which is determined by answers to the folloiwng questions:
| Question | Answer | Integrity Target |
| Data Accuracy | Not Applicable | 0 |
| Data Accuracy | Not Important | 0 |
| Data Accuracy | Moderately Important | 4 |
| Data Accuracy | Very Important | 7 |
| Data Accuracy | Vitally Important | 10 |
And an Actual  which is determined by what controls are in place to protect the data. The score of each control is added up to make the Actual
which is determined by what controls are in place to protect the data. The score of each control is added up to make the Actual 
| Question | Answer | Integrity Score |
| Application Logs | No | 0.0 |
| Application Logs | Yes | 0.50 |
| Application Logs | Yes and logs are monitored for unusual activity | 1.0 |
| Backup & Recovery | No Backups | 0.0 |
| Backup & Recovery | Irregular Backups | 0.50 |
| Backup & Recovery | Not Applicable | 1.0 |
| Backup & Recovery | Scheduled Backups | 1.0 |
| Equipment Access | Telnet | 0.0 |
| Equipment Access | Remote Desktop | 0.0 |
| Equipment Access | Other | 0.0 |
| Equipment Access | SSH | 1.0 |
| Equipment Access | Other Encrypted | 1.0 |
| Equipment Access | Not Applicable | 2.0 |
| Equipment Access | Console Only | 2.0 |
| Equipment Access IP Restrictions | No Restrictions | 0.0 |
| Equipment Access IP Restrictions | Restricted to organisation IP addresses | 0.25 |
| Equipment Access IP Restrictions | Not Applicable | 0.50 |
| Equipment Access IP Restrictions | Restricted to engineers IP addresses | 0.50 |
| Equipment Access IP Restrictions | No Network Connection | 0.75 |
| Equipment Location | Office/Location (Unsecured) | 0.0 |
| Equipment Location | Office/Location (Secured) | 0.25 |
| Equipment Location | Communications Room | 0.50 |
| Equipment Location | Not Applicable | 0.75 |
| Equipment Location | Secure Data Centre (Single) | 0.75 |
| Equipment Location | Secure Data Centres (Multiple) | 0.75 |
| Firewall | No | 0.0 |
| Firewall | Not Applicable | 1.0 |
| Firewall | Restricted by firewall or ACL | 1.0 |
| Incident Logging | No Formal Process | 0.0 |
| Incident Logging | Other | 0.50 |
| Incident Logging | Incident Management System e.g. LANDesk | 1.0 |
| Lifecycle | Emerging | 0.0 |
| Lifecycle | Retire | 0.0 |
| Lifecycle | Contain | 0.50 |
| Lifecycle | Core | 1.0 |
| Service Monitoring | No | 0.0 |
| Service Monitoring | Not Applicable | 0.50 |
| Service Monitoring | Yes | 0.50 |
| Service Monitoring | Yes With email or SMS alerting | 1.0 |
| Service Type | Other | 0.0 |
| Service Type | Bespoke | 0.0 |
| Service Type | Cloud | 1.0 |
| Service Type | Commercial Off The Shelf (COTS) | 1.0 |
| Service Type | Open Source | 1.0 |
| User Interface Connection | Connects Over Network (e.g. HTTP) | 0.0 |
| User Interface Connection | Not Applicable | 1.0 |
| User Interface Connection | Runs On Local PC | 1.0 |
| User Interface Connection | Client/Server type connection | 1.0 |
| User Interface Connection | Connects Over Secure Network (e.g. HTTPS) | 1.0 |
| User Interface IP Restrictions | No Restrictions | 0.0 |
| User Interface IP Restrictions | Restricted to Organisation IP addresses | 1.0 |
| User Interface IP Restrictions | Restricted by Port | 1.0 |
| User Interface IP Restrictions | Restricted to a subset of Organisation IP addresses | 1.25 |
| User Interface IP Restrictions | Not Applicable | 1.50 |
| User Interface IP Restrictions | No Network Access | 1.50 |
| User Interface Login | No Usernames or Passwords | 0.0 |
| User Interface Login | Cloud Usernames & Passwords (Google/Other) | 0.25 |
| User Interface Login | Windows Login | 0.50 |
| User Interface Login | Local Usernames & Passwords | 0.75 |
| User Interface Login | Not Applicable | 1.0 |
| User Interface Login | Central Organisation Usernames & Passwords | 1.0 |
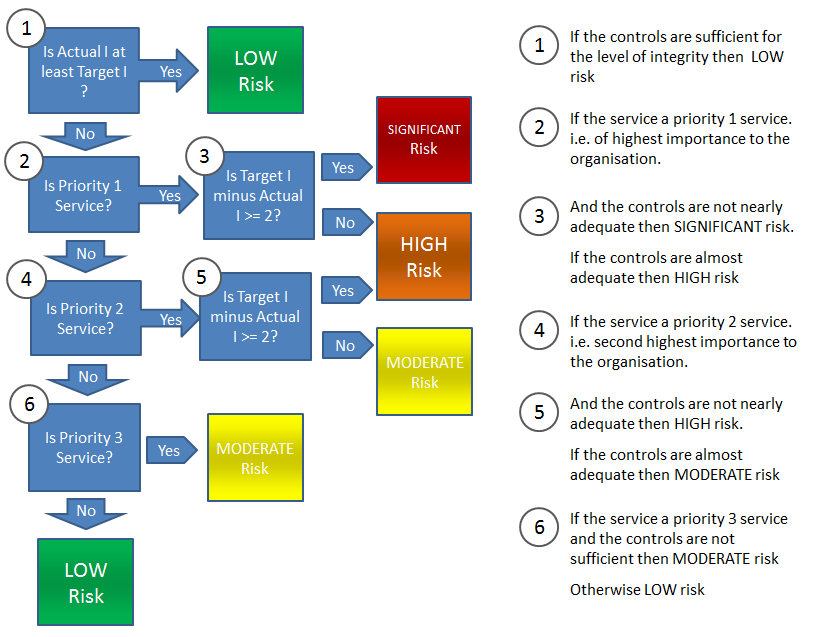
Integrity Workflow
When the Target  and the Actual
and the Actual  are known, the following workflow is performed to calculate the residual integrity risk.
are known, the following workflow is performed to calculate the residual integrity risk.
 The integrity workflow uses the service priority, which is how important the service is to the organisation. More informartion here: Service Restoration Priorities
The integrity workflow uses the service priority, which is how important the service is to the organisation. More informartion here: Service Restoration Priorities
IT Risk Audit - Availability
Availability, or uptime will vary for each service. The eLearning system might need to be up 24x7, whilst the time sheeting system doesn't have to be as reliable.
For each service we want to set a Target  which is determined by answers to the following questions:
which is determined by answers to the following questions:
| Question | Answer | Availability Target |
| Business Impact of Service Outage | There Will Be No Impact On The Business If This Service Is Down | 0 |
| Business Impact of Service Outage | Service Can Be Down For No More Than 1 Day | 5 |
| Business Impact of Service Outage | Service Can Be Down For No More Than 4 Hours | 7 |
| Business Impact of Service Outage | Service Can Be Down For No More Than 1 Hour | 8 |
| Business Impact of Service Outage | Service Can Only Be Down For Scheduled Maintenance | 8 |
| Business Impact of Service Outage | Service Cannot Be Down For Any Period | 9 |
And the following is added to the availability target
| Question | Answer | Availability Target |
| Service Uptime hour requirements | Business Hours Only | 0.5 |
| Service Uptime hour requirements | 24 Hours | 1 |
The Actual  which is determined by what controls are in place to keep the service available. The score of each control is added up to make the Actual
which is determined by what controls are in place to keep the service available. The score of each control is added up to make the Actual 
| Question | Answer | Integrity Score |
| Application Logs | No | 0.0 |
| Application Logs | Yes | 0.50 |
| Application Logs | Yes and logs are monitored for unusual activity | 1.0 |
| Backup & Recovery | No Backups | 0.0 |
| Backup & Recovery | Irregular Backups | 0.50 |
| Backup & Recovery | Not Applicable | 1.0 |
| Backup & Recovery | Scheduled Backups | 1.0 |
| Equipment Access | Telnet | 0.0 |
| Equipment Access | Remote Desktop | 0.0 |
| Equipment Access | Other | 0.0 |
| Equipment Access | SSH | 1.0 |
| Equipment Access | Other Encrypted | 1.0 |
| Equipment Access | Not Applicable | 2.0 |
| Equipment Access | Console Only | 2.0 |
| Equipment Access IP Restrictions | No Restrictions | 0.0 |
| Equipment Access IP Restrictions | Restricted to organisation IP addresses | 0.25 |
| Equipment Access IP Restrictions | Not Applicable | 0.50 |
| Equipment Access IP Restrictions | Restricted to engineers IP addresses | 0.50 |
| Equipment Access IP Restrictions | No Network Connection | 0.75 |
| Equipment Location | Office/Location (UnSecured) | 0.0 |
| Equipment Location | Office/Location (Secured) | 0.25 |
| Equipment Location | Communications Room | 0.50 |
| Equipment Location | Not Applicable | 0.75 |
| Equipment Location | Secure Data Centre (Single) | 0.75 |
| Equipment Location | Secure Data Centres (Multiple) | 0.75 |
| Firewall | No | 0.0 |
| Firewall | Not Applicable | 1.0 |
| Firewall | Restricted by firewall or ACL | 1.0 |
| Incident Logging | No Formal Process | 0.0 |
| Incident Logging | Other | 0.50 |
| Incident Logging | Incident Management System e.g. LANDesk | 1.0 |
| Lifecycle | Emerging | 0.0 |
| Lifecycle | Retire | 0.0 |
| Lifecycle | Contain | 0.50 |
| Lifecycle | Core | 1.0 |
| Service Monitoring | No | 0.0 |
| Service Monitoring | Not Applicable | 0.50 |
| Service Monitoring | Yes | 0.50 |
| Service Monitoring | Yes With email or SMS alerting | 1.0 |
| Service Type | Other | 0.0 |
| Service Type | Bespoke | 0.0 |
| Service Type | Cloud | 1.0 |
| Service Type | Commercial Off The Shelf (COTS) | 1.0 |
| Service Type | Open Source | 1.0 |
| User Interface Connection | Connects Over Network (e.g. HTTP) | 0.0 |
| User Interface Connection | Not Applicable | 1.0 |
| User Interface Connection | Runs On Local PC | 1.0 |
| User Interface Connection | Client/Server type connection | 1.0 |
| User Interface Connection | Connects Over Secure Network (e.g. HTTPS) | 1.0 |
| User Interface IP Restrictions | No Restrictions | 0.0 |
| User Interface IP Restrictions | Restricted to Organisation IP addresses | 1.0 |
| User Interface IP Restrictions | Restricted by Port | 1.0 |
| User Interface IP Restrictions | Restricted to a subset of Organisation IP addresses | 1.25 |
| User Interface IP Restrictions | Not Applicable | 1.50 |
| User Interface IP Restrictions | No Network Access | 1.50 |
| User Interface Login | No Usernames or Passwords | 0.0 |
| User Interface Login | Cloud Usernames & Passwords (Google/Other) | 0.25 |
| User Interface Login | Windows Login | 0.50 |
| User Interface Login | Local Usernames & Passwords | 0.75 |
| User Interface Login | Not Applicable | 1.0 |
| User Interface Login | Central Organisation Usernames & Passwords | 1.0 |
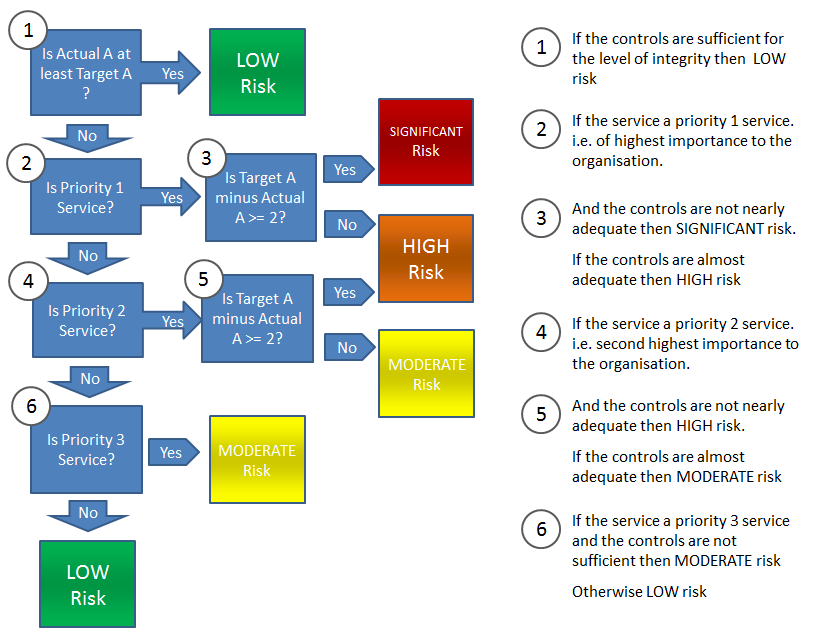
When the Target  and the Actual
and the Actual  are known, the following workflow is performed to calculate the residual availability risk.
are known, the following workflow is performed to calculate the residual availability risk.
 The availability workflow uses the service priority, which is how important the service is to the organisation. More informartion here: Service Restoration Priorities
The availability workflow uses the service priority, which is how important the service is to the organisation. More informartion here: Service Restoration Priorities
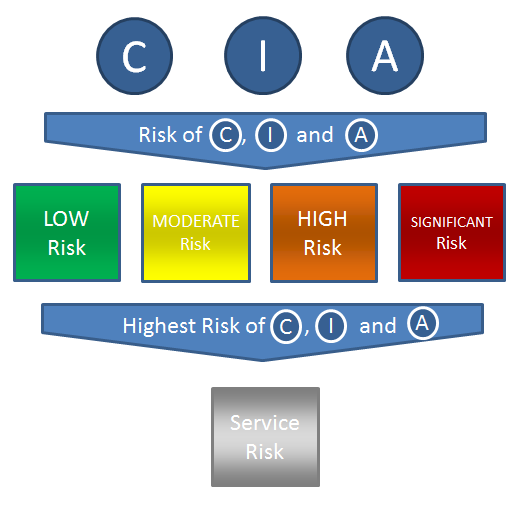
IT Risk Audit - Overall Residual Risk
Once the Confidentiality, the Integrity and the Availability risks are known the highest of the three becomes the overall service residual risk.
Generating Complete Risk Reports
To generate a complete risk report use the Risk Report link in the Reports side menu.

By combining all the services, the service dependencies, the target CIA's, the actual CIA's, the data stored and the priority of each service, ServiceView can generate a complete risk report.
Unlike the "Risk Classification" tab for each service this report takes into count the risks of underpinning services and how that might affect the availability of high priority services.
The first page is a summary of risks and high priority services, then there is a one page report on each service indicating its risk level, a service register documenting each service and its purpose. Following those is an Information Asset Register detailing which IT services store which data types, this is required by law in most countries, and lastly a Technology Asset Register organising service by their technology.
Generating a Report for Risk Data Completion
To create a report for viewing the completion status of the risk data per service, the user needs to logged in as a admin user.
Click on the Admin tab and go to Reports.
On the reports page, click the drop down menu and choose Service Field Population Percentage. Then click generate report.

This will list the service name, complete percent, service owner and technical owner.
The data can then be downloaded into a spread sheet by clicking the download data button in the top right.